Egyptian gods have definitely bewitched the creators of Locky ransomware – during the last couple of weeks security experts discovered two different viruses having the names “borrowed” from Norse gods. Each of them promotes the special decrypt tool called Locky decrypter that is needed to “unlock” encrypted files. If you have ever been attacked by ransomware and lost your files, you can be convinced that this tool is the only way to recover your files. However, security experts have been working hard on free decrypters and special software that could help people prevent the money loss. So, if you got infected with ransomware, don’t rush with making a payment to cyber criminals because you have more options than you think. However, ransomware prevention is still important as you cannot know how powerful each of Locky versions and similar file-encrypting viruses are.
The first ransom-demanding virus you should be especially careful with is known as Aesir ransomware. This malware showed up in the end of November but scammers didn’t distribute it actively from the first day of its appearance. The first victim of Aesir virus contacted us only in December 2016. Typically, this ransomware appends .aesir file extension to each of its target files and starts showing its ransom note that demands several hundreds of dollars. This malware is capable of affecting around 456 different file types, so the most of its victims are left with nothing. The main method used for its distribution relies on spam and fake Facebook messages offering their victims to check the file titled as Photo_[4 random numbers].svg. Of course, you should stay away from such offers.
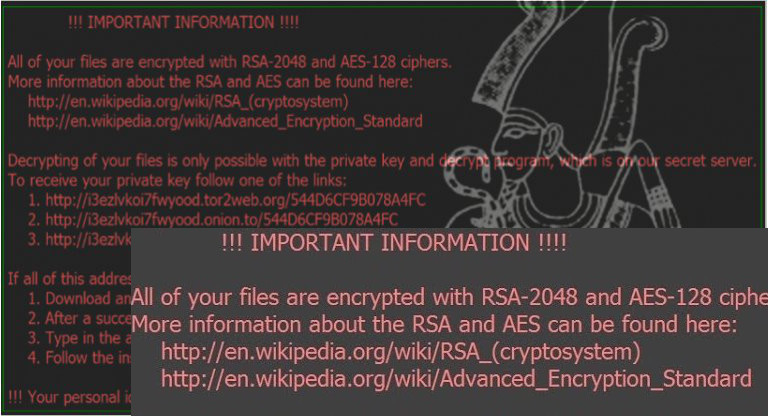
However, it seems that Aesir ransomware will soon be surpassed by Osiris ransomware. This malware showed up in the beginning of December and, since then, has been actively spreading around. The main fact that you should remember about this ransomware is that it provides the special identification number to each of its victims which is a set of these symbols: [8 symbols]–[4 symbols]–[4 symbols]–[8 random symbols]–[12 random symbols]. Just like the name of this ransomware suggests, it appends .osiris file extension to the target files and claims that the only way to decrypt encrypted files is to buy the Locky decrypter. Unfortunately, this virus can hardly be detected by the most of anti-virus software – only 8 out of 56 scanners managed to detect it. To prevent infiltration of Osiris, you need to be very careful with spam because this is the main distribution method of this ransomware.
