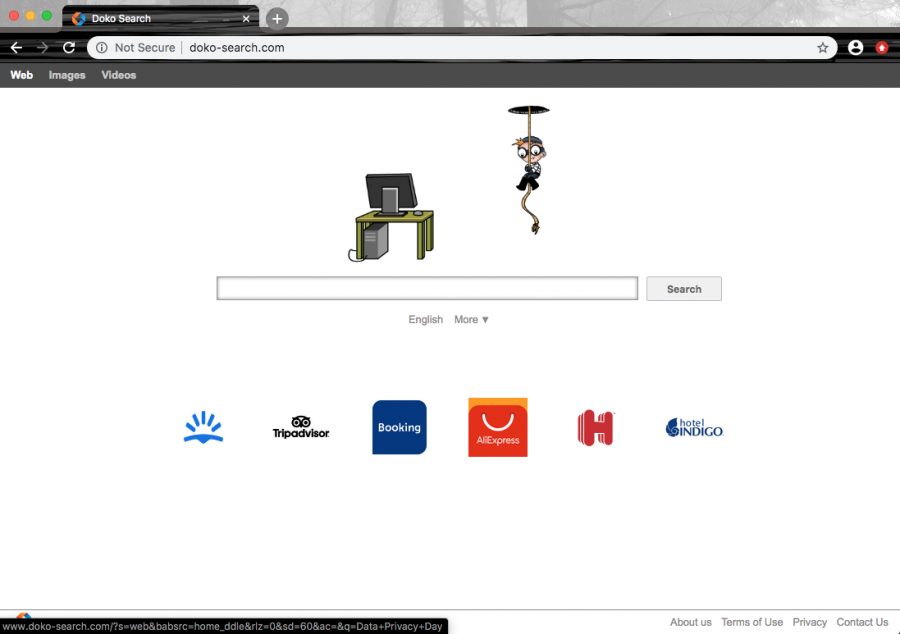
Deceiving domain - doko-search.com
Doko-search.com is considered to be a browser hijacker that travels by employing deceptive distribution techniques such as "software bundling". This type of product can come included in freeware and shareware packages that are downloaded from third-party websites such as cnet.com, download.com, and softonic.com.
Doko-search.com virus can perform unexpected changes in browser settings such as the default search provider, homepage, and new tab URL. As a result, the user is forced to use the new search engine that can load altered search query results. These types of modifications can be diminished only be permanently eliminating the browser hijacker.
Furthermore, the developers who promote doko-search.com aim to gather monetary income from the advertisements the app provides. You can easily get loaded with various offers and deals to purchase rogue security software and subscribe to useless services.
Continuously, doko-search.com can record browsing-related information as this type of activity might also provide income if the collected non-personal details are shared with other parties. Nevertheless, the gathered data can do a great part in targeted advertising campaigns.
| Name | Doko-search.com |
|---|---|
| Type | Browser hijacker |
| Distribution | This suspicious product mostly gets delivered through the "software bundling" technique and comes with freeware or shareware that has been downloaded from third-party sources such as cnet.com, download.com, and softonic.com |
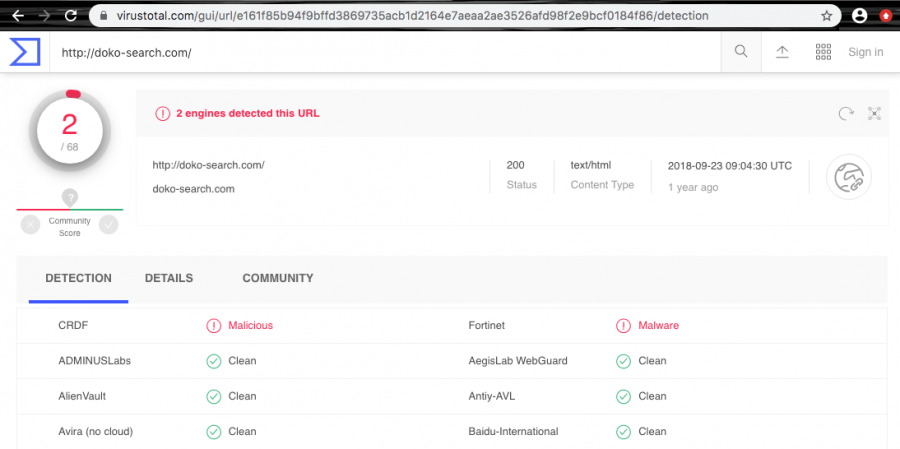
| Detections | According to VirusTotal information, this browser hijacker has been spotted as malware by two AV programs called CRDF and Fortinet |
doko-search.com violations
2CR-015: The suspicious domain has been detected as malicious by CRDF and Fortinet AV tools
2CR-004: The browser hijacker modifies major settings such as the default search engine, new tab URL bar, and the homepage of the hijacked web browser