KEYPASS ransomware is a serious threat as it is not a typical ransomware
Ransomware virus that encrypts your data and demands for a ransom has more harmful features than it appears in the first instance. This not so typical Keypass ransomware has a hidden feature that needs to be activated by pressing a certain button on the keyboard. Default hides this manual control feature but after the key is pressed hackers become capable of changing various characteristics of the ransomware itself.
With this remote access, the attackers can customize the whole encryption process. Modifying parameters like victims’ ID, file extension or ransom note text makes this virus customizable and more dangerous than any other ransomware. The virus runs automatically and behaves as other crypto-extortionists, but this added feature may be the indicator that developers behind this malware had planned to use the program in manual attacks right of the bat.
Ransomware features
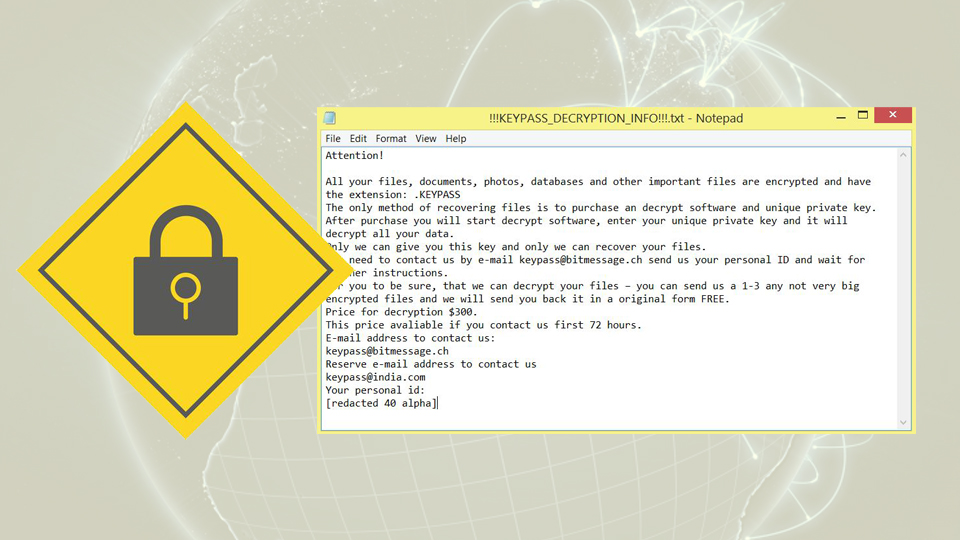
KEYPASS ransomware is a file encrypting virus that uses AES encryption method while changing the file appendix to .keypass from the original one. This makes data useless and possibly damaged. After successful encryption, virus places a note containing the information about this attack and the amount of demanded ransom, contact information. !!!KEYPASS_DECRYPTION_INFO!!!.txt file details that people need to pay $300 in Bitcoin to get their files decrypted. However, this may be not true. You are not advised to contact these criminals or paying the ransom because they may never be trusted.
Also, the developers of this virus offer you to send them a few files with the opportunity of free decryption. This often makes people believe that the people behind this are trustworthy. Cybercriminals want you to think that. They provided the contact emails for people in the ransom note. This also makes them look more “professional” and trustful.
Different threat same solution
You can get various cyber infections and malware that comes to your system in multiple ways. Something like unwanted programs can get on your device during insecure installation, and something as big as the ransomware infiltrates the system from spam email attachments or directly via system vulnerabilities. But all these cyber infections can be removed using the same malware-fighting software.
Anti-malware tools can detect ransomware and other threats on your device and remove them quickly. It is important to use reputable programs so you can trust them and be sure that every little possible threat is eliminated. Since these intruders come silently, you may have more than you think and a full system scan with proper tools help you to clean your computer system thoroughly.
