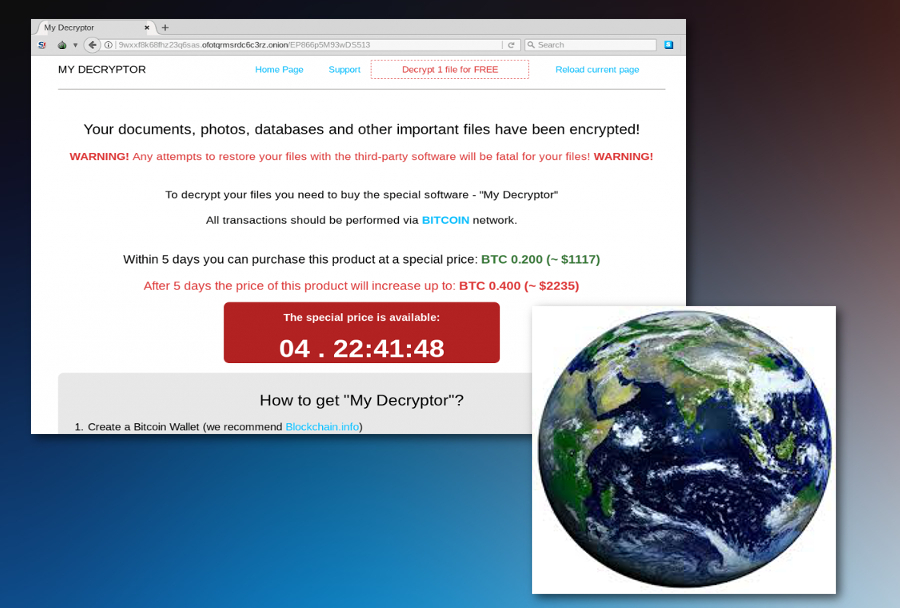
Magniber ransomware expands outside South Korea with a changed exploit kit
Magniber ransomware firstly attacked people at the end of 2017. This crypto-virus uses Magnitude exploit kit, and its activity started in South Korea. Right now this virus expands to other Asian countries with a slightly changed encryption code. After nine months this virus came back and targeted Taiwan, Hong Kong, and other countries.
First, Magniber ransomware targeted people located in South Korea and with specific language settings on the PC, but some of the users were infected while traveling outside the country. Also, there were some speculations earlier, about it spreading further, but no confirmation. At the beginning of July 2018 researchers discovered some changes in the binary code of this ransomware and affected users’ outside South Korea.
Entire source code right now is evolved and more complicated. This makes Magnitude exploit kit higher quality. According to researchers virus developers no longer depend on the only C&C server or hardcoded key for the encryption process. It uses more refined techniques.
The same exploit kit as Cerber ransomware
Magnitude exploit kit was known from 2013, and in October 2017 it was used in the development of the Magniber ransomware. The similar name comes from a connection between the two. The same exploit kit was used to infect victims with Cerber ransomware. This virus targeted people all over the world.
This “positive” change in coding and improved ransomware version tells about the evolving and possibility to expand to more countries. This version now is in the similar level of quality and danger as Cerber ransomware versions. As it is known this exploit kit has been developed for quite some time but quickly patched when appeared.
Magniber ransomware in previous attacks formed a nine letter appendix to encrypted files. This latest, evolved version came with .dyaaghemy file extension. Previous versions of both of these ransom-based viruses had decryption tools but no known method to recover encrypted files right now.
There is a way to avoid ransomware
The most common way of ransomware spreading is spam email attachments. These letters often are filled with useless commercial content, and attached files can be infected with various threats. Immediately after downloading and opening them on your PC you get malware. You can avoid this by being cautious and deleting them without reading and opening.
There is another way of virus spreading when talking about ransomware. Exploit kits as upper-mentioned Magnitude is more sophisticated. The main thing about this method is compromising selected domains. By injecting scripts into websites hackers can access users’ devices.
The best way of prevention is cybersecurity tools and programs. Anti-virus, anti-spyware and anti-malware programs can be a vaccine and a cure when dealing with ransomware. These tools can perform a full system scan on the PC, detect malware after and before the attack. You can avoid the initial attack or any infection repetition.
