Cyber security experts advise users to arm their computers with powerful anti-malware programs and start creating data backups in case they haven’t done it yet. According to reports, the third variant of the infamous WannaCry ransomware is making rounds on the Internet. There aren’t many details about WannaCry 3.0 yet, so it is unknown how the latest malware variant spreads or acts. The only thing is known that the virus clearly expresses cybercriminals greed as it helds victim’s data to ransom. If you would like to follow the latest news about the virus, we suggest following the news on 2-Spyware site – to be precise, the article about WannaCry 3.0 ransomware virus.
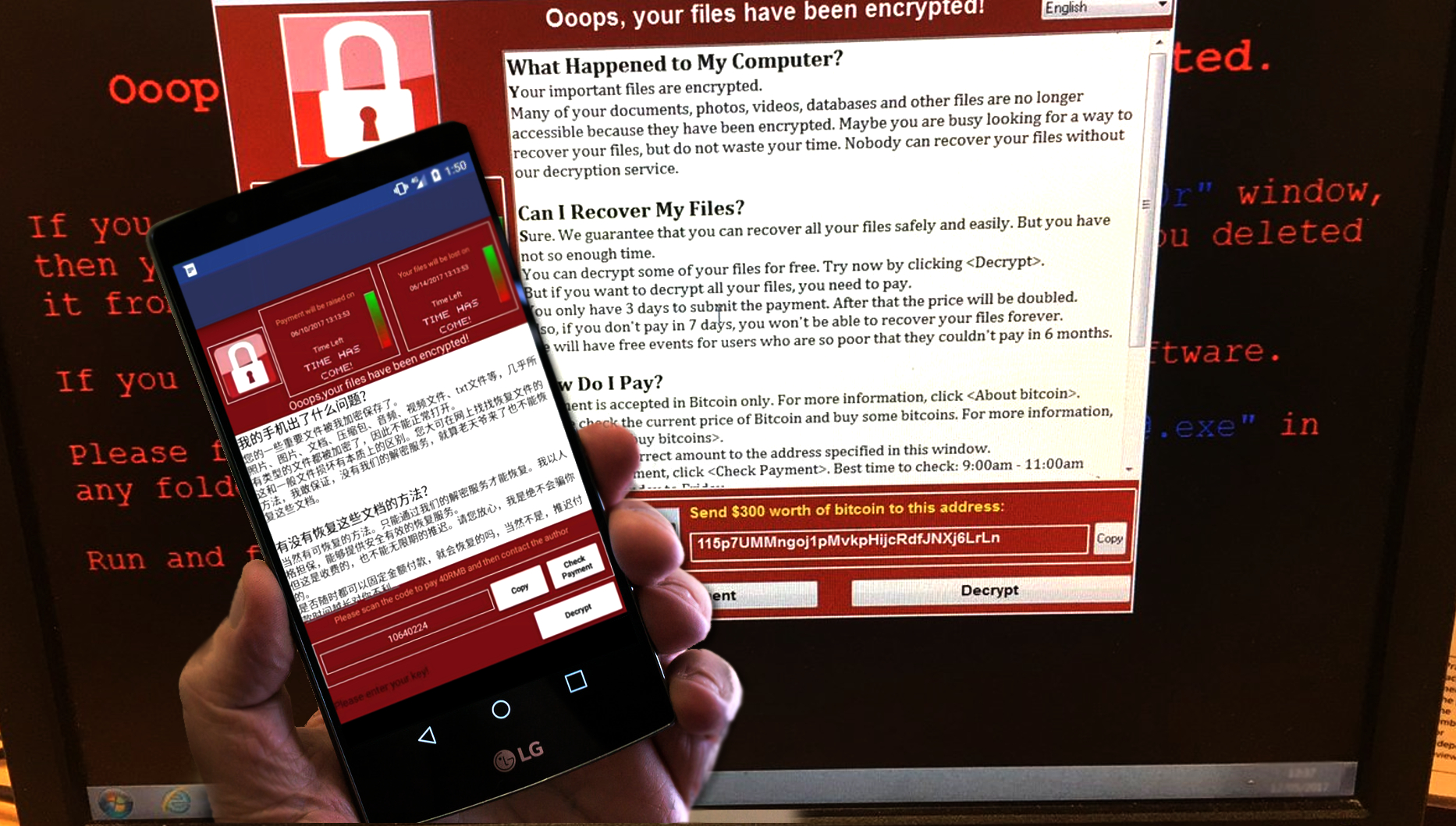
Speaking of the initial WannaCry ransomware attack, it was one of the biggest cyber attacks launched ever, and it managed to infect a whopping 400,000 computers worldwide. Further analysis revealed that the majority of these computers were running Windows 7 versions. The virus can be identified from extensions it leaves on the corrupted data ((.wcry, .wncry, .wncryt, .wcrypt) and the ransom note (@[email protected] or Please Read Me!.txt file). The virus earned approximately $140,000 since its first appearance, and this number just keeps growing. There is no need to say that developers of this ransomware know what they’re doing. It is very close to Cerber’s earnings, which earns more or less $200k a month with the help of an affiliate system. However, the author of the ransomware gets 40% of the affiliate revenue only.
Ransomware commonly attacks Windows computers, although there are versions for Macs or Android smartphones as well. It didn’t take long for criminals (they are not related to real WannaCrypt0r’s developers) to create a copycat version for Android OS. The Android version of the ransomware is called WannaLocker, and it is distributed via Chinese gaming forums. Reportedly, criminals present it as a plugin for King of Glory game. Following a successful infiltration, the malicious application removes itself from Android apps folder and replaces phone’s wallpaper with an anime-themed picture. Then the smartphone virus encrypts data stored on smartphone’s external storage. It targets every file with .jpeg, .jpg, .png, .bmp, .gif, .pdf, .doc, .docx, .txt, .avi, .mkv, .3gp, or .mp4 file extension. The virus then asks to pay 5-6 USD using WeChat, QQ, or AliPay.
