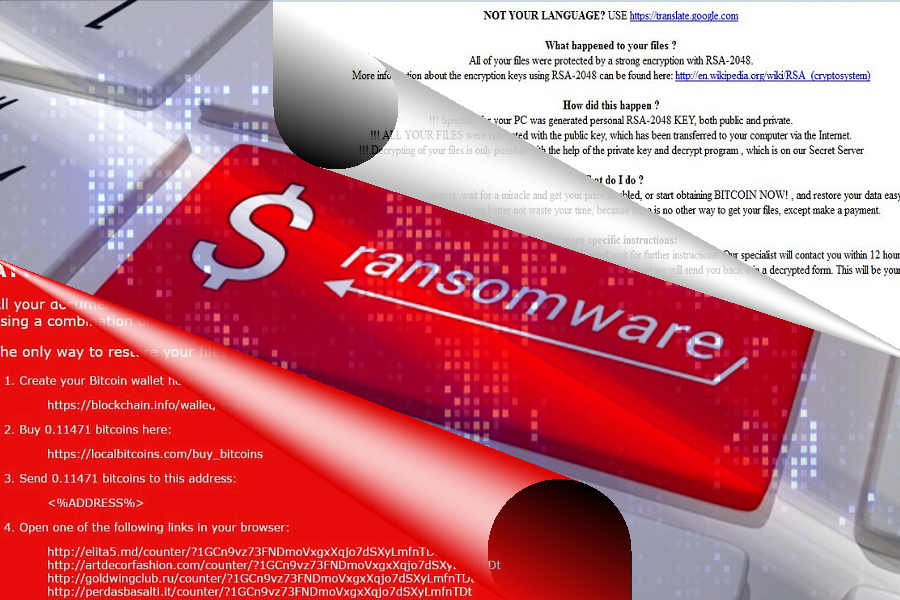
Evolution of older crypto-malware
Upgrading old threats from the very root is becoming a common practice among cyber criminals. After another wave of Petya dashed through the cyber space, developers of less known threats are making a move as well.
CryptoMix hackers remain persistent
If you have been following IT news, you might be well aware of Nemucod, AES and CryptoMix threats. The story of the Cryptomix is especially amusing. After IT experts have continuously cracked the decryption code, the owners remained persistent and kept programming new versions.
On July 2017 the developers launched an updated version which leaves its mark by appending .exte file extension. What is more, current versions are able to function offline. This family of threats has kept steadily evolving. After IT experts put a checkmate on Mole02 threat, the hackers struck with Azer threat. The distribution technique of this malware is not exceptional, unlike Nemucod-AES threat.
The hybrid of Nemucod-AES emerges
Some of you might be familiar with Neutrino, Angler and RIG exploit kits. They are responsible for the transmission of such notorious ransomware as Cerber, TeslaCrypt, and few others.
Though Neutrino was known as the exploit kit, fraudsters decided to make use of its notorious name for other purposes. Likewise, the mixture of Nemucod and AES has been born. Besides its complex structure, its methods of the transmission trigger more interest.
Along with spreading via corrupted applications, links and exploit kits, the malware targets gullible users via UPS scam messages. They warn users about an undelivered parcel and tempt them to extract the malware disguised in the attached file. Fortunately, Emsisoft experts have found vulnerabilities in the malware and devised a free decryption tool for their victims.
Finding countermeasures
The fact that former less active and seemingly curbed infections are rising again is surely an alarming sign. Hackers add new ways of distribution and develop more cunning hijack techniques.
Thus, you never know when formerly treated as weak ransomware might evolve into the cyber issue. In order to stand our ground against continuous cyber threats, digital protection by the cyber tool is not sufficient. Vigilance plays a significant role in the cyber security as well.
