Globe Imposter ransomware actively attacks computers in the United States and Europe
Discovered at the end of 2016, Globe Imposter ransomware continues spreading in 2017. Researchers noticed that steady increase of the virus distribution during the past 30 days. The majority of attacks were held in the United States and Europe.
This file-encrypting virus is a copy of a Globe ransomware. It was updated several times. Nevertheless, new variants append different file extensions to the targeted files; cyber criminals slightly changed distribution strategy as well.
The latest variants that appeared on 2017 are known as .ocean file extension virus, A1Lock virus and .Write_me_[[email protected]] file extension virus. Malware together with its updates mostly spreads via malicious spam emails that include fake payment receipts.
Malspam campaigns actively spread malicious program
Malware analysts have noticed an increased activity of malicious emails spreading Globe Imposter across the United States and European countries. Since the beginning, this strategy was the main distribution method of the ransomware. However, it also spreads via drive-by downloads and malvertising.
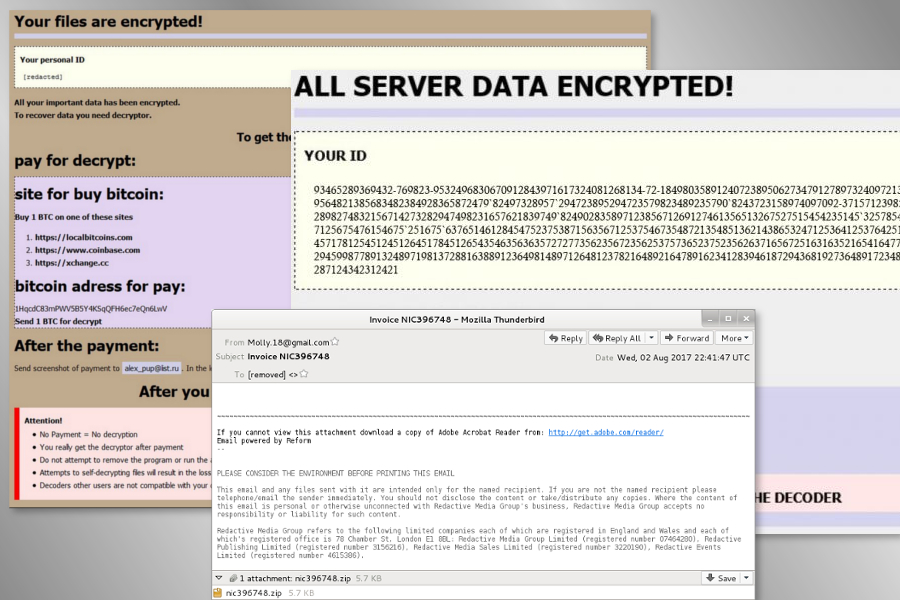
The recently discovered malspam campaign seems to be based on the infamous Necrus botnet that was responsible for spreading Locky ransomware. Currently, Globe Imposter virus spreads via fake emails that include zip archive. These malicious attachments are renamed as “Payment Receipt” and include random digits or/and letters, for instance:
- Payment Receipt_72537 — P72537.zip,
- Payment Receipt#039 — P039.zip,
- Payment-59559 — P59559.zip.
These zip archives include malicious .vbs file that is responsible for activating and running ransomware on the computer. However, older malspam campaigns spread obfuscated .js file. These dangerous emails have subject lines “Voice Message Attached,” “Scanned Image,” or “Invoice [random characters].”
Therefore, before rushing to click an unknown receipt or other important documents, you have to make sure that it’s safe to do it. If you do not expect to receive such email, do not open it. Keep in mind that crooks might use social engineering and pretend to be from reliable companies, so it’s important to double-check information before opening any unfamiliar content.
The main facts of the Globe Imposter and its removal
The Globe Imposter uses AES 256 encryption algorithm to corrupt files on the targeted computer. Originally, the virus appends .crypt file extension. However, its variants can append numerous different suffixes to the targeted files, for instance, .wallet, nCrypt, .[[email protected]]SON, etc.
Following data encryption, it might drop a ransom note where crooks tell about data recovery options. The letter by cyber criminals might be named as:
- HOW_OPEN_FILES.hta, how_to_back_files.html,
- RECOVER-FILES.html, !back_files!.html,
- #HOW_DECRYPT_FILES#.html.
Nevertheless, that crooks tell to contact them via provided email address and transfer the ransom in Bitcoins; you should not do it. Security researchers have already created a free decryptor that helps to recover files after Globe Imposter attack. Therefore, as soon as you learn about hacked computer, you should focus on virus removal.
This malicious program should be uninstalled using professional security software. If you have some difficulties with removal, check Globe Imposter elimination guidelines on 2-spyware.
