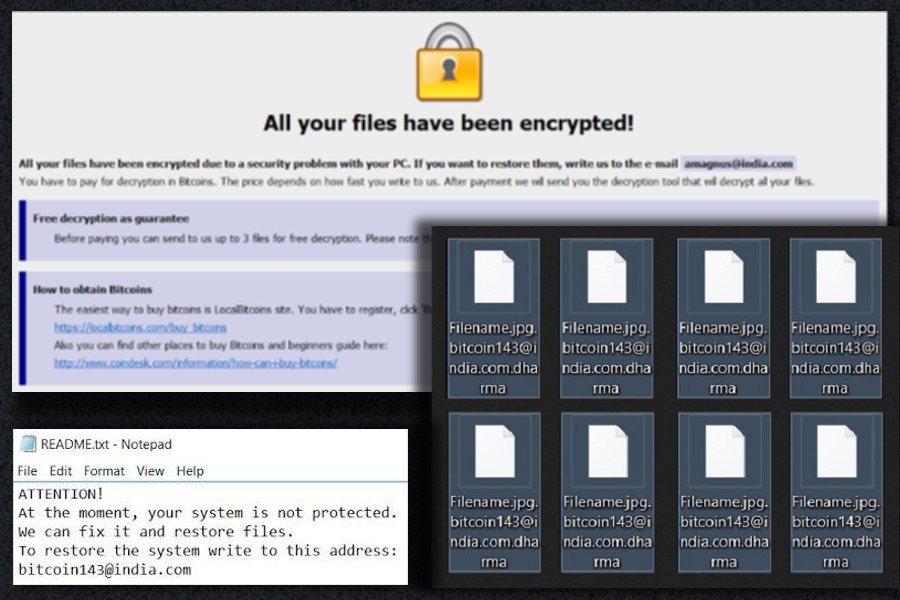
Since the November 2016, Dharma ransomware along with its other variants have been threatening computer users and taking their files to hostage. Malware has already left thousands of people without the possibility to access their files without paying the ransom. We are all aware of the fact that there’s no guarantee that transferring some Bitcoins may not help to get personal documents back. Fortunately, there are few data recovery methods that may help those who are looking for free and safe data recovery solutions. What is more, it seems that one of the virus versions have a bug which allows victims to restore their files simply using 7-ZIP. 2-spyware researchers’ team receive a comment from a person that claims that this method has helped to restore one of his customer’s data.
During data encryption, Dharma distorts files by appending particular file extension and contact email address to each targeted file. Malware might append .dharma, .wallet or .zzzzz file extensions, and one of these email addresses: [email protected], [email protected] or [email protected]. However, the virus version that appends .[[email protected]].dharma file extension might have a bug that allows simple data recovery solution. Simple as that, victims can extract files with 7-Zip. Therefore, if this cyber parasite took your files to the hostage, we highly recommend trying this method and getting back your files for free.
Talking about other data recovery possibilities, the situation hasn’t changed yet. The official decryptor hasn’t been released yet. However, it’s unknown whether 7-Zip can extract files that have different file extension appended by Dharma. What is more, the virus is associated with CrySiS ransomware which is already decryptable. Hence, its decrypter might help for some victims of ransomware. People, who don’t have data backups, should try additional data recovery methods, for instance, using Data Recovery Pro tool. Sometimes victims can rescue their files using Windows Previous Versions feature or relying on ShadowExplorer that extracts data from Shadow Volume Copies. If you need detailed instructions how to use these methods, you can find them here. However, don’t forget that before trying them, you have to remove the virus!
