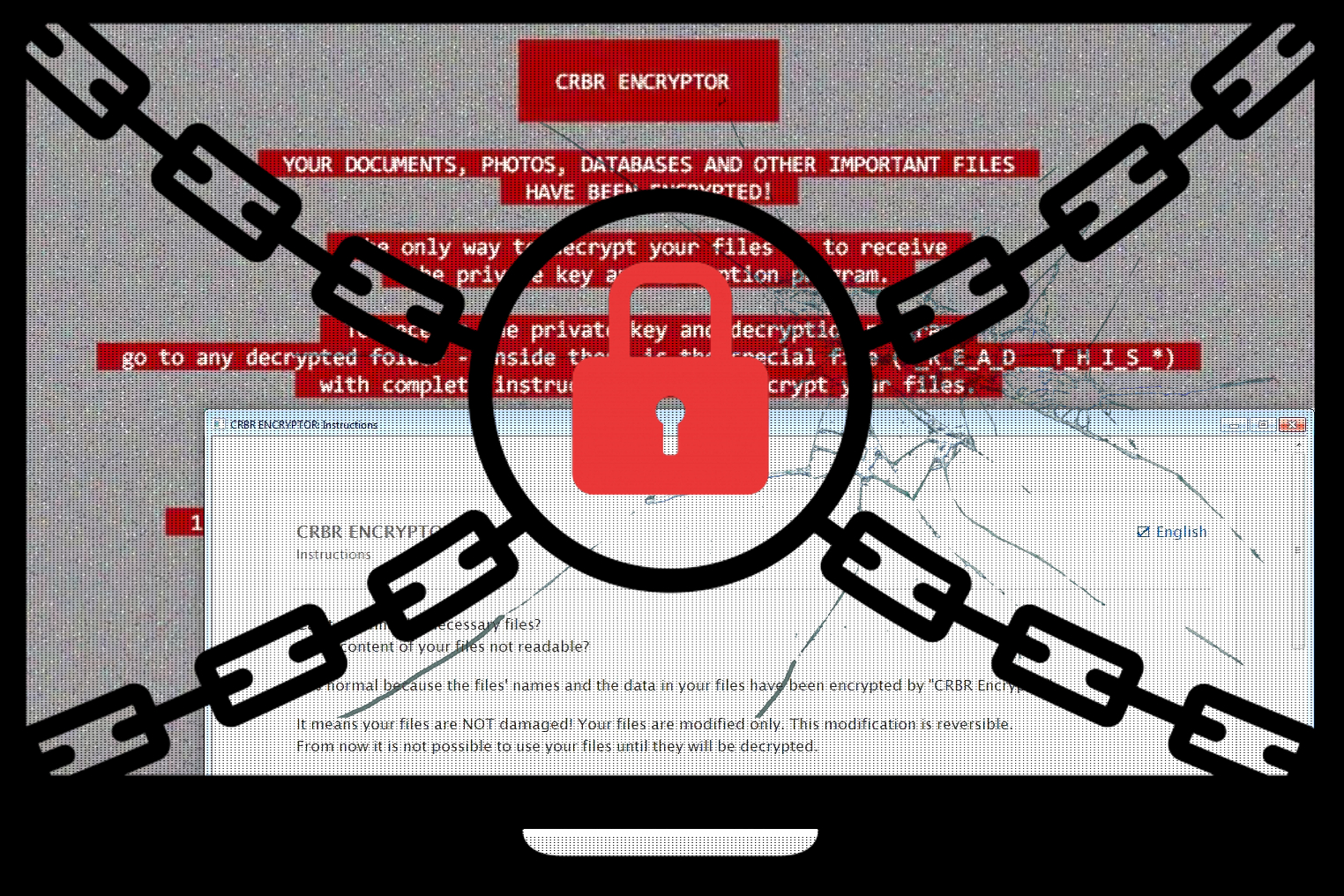
Cerber ransomware is at full strength – steals passwords and Bitcoins
Cerber ransomware (also found as CRBR ENCRYPTOR) is now stronger than ever – since it teamed up with Kovter, Boaxxee, and Nymaim Trojan, it became probably the most fearsome computer virus available today. Now, the ransomware comes with additional features such as:
- Ability to steal private information – logins, passwords;
- Ability to steal private files, including files of these Bitcoin wallet applications – Bitcoin (wallet.dat), Multibit (*.wallet) and Electrum (electrum.dat).
Cerber developers are trying to steal everything valuable from victims’ computers
The virus performs data theft before running the process responsible for data encryption. It grabs saved passwords from Mozilla Firefox, Google Chrome and Internet Explorer browsers. Then it finds files associated with cryptocurrency wallet applications and sends all gathered data to criminals’ Command & Control server. The virus then deletes the files and starts the encryption process.
Such features show that ransomware developers are testing new ways of monetizing the Cerber virus. It must be noted that the attackers cannot steal cryptocurrency from victims’ accounts without having passwords to them, however, they might be able to access them, considering that they also grab all saved passwords from web browsers.
It is extremely important to secure your computer and have a data backup. In case of a ransomware attack, the backup helps to recover the majority of encrypted files for free.
However, the rapidly evolving virus is highly sophisticated, so in order to make your anti-malware programs capable of identifying its latest versions, you have to continuously update your security software or simply enable automatic updates for it. For more anti-ransomware tips, we suggest visiting 2-Spyware.com website.
Distribution of the latest Cerber variant
On August 2, cyber security researchers noticed increased CRBR activity. It became clear that the ransomware is being pushed by Magnitude exploit kit, which is used to attack certain Asia countries only. According to researchers, the virus mainly targets South Korea.
While “exploit kit” sounds somehow complicated, we can provide a simpler explanation of how Cerber can infect your computer. The ransomware developers use various tricks to make ad agencies trust them and let them add their malicious ads to their servers.
As a result, legitimate websites that display ads from that ad network can display a malicious ad that, once clicked, redirect the user to malicious Magnitude exploit kit site, where the Cerber ransomware hides.
This way, by simply clicking on an Internet ad, the victim can install the ransomware without realizing it. It is even more likely to happen if the victim doesn’t have a security software installed on the computer.
