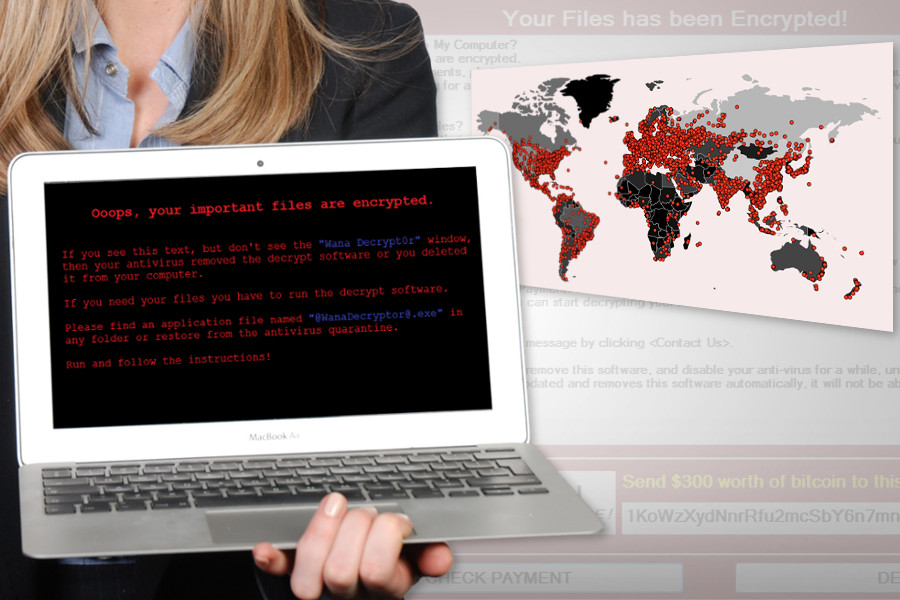
The past couple of days were eventful and terrifying in the online community. The 12th of May marks one of the biggest cyber attacks in 2017. Last Friday cyber criminals started spreading WannaCry by exploiting Windows operating system vulnerability. Distribution of the malware has been slowed down by activating “kill switch” function. However, cyber criminals did not give up and released WannaCry 2.0 ransomware. Numerous WannaCry variants and updates have been showing up since Sunday. Malware has already infected more than 230,000 computer users in 150 countries, and the number of attacks continues to grow. Ransomware successfully attacked numerous companies, public sector, and home computer users. What could make this malware so successful? It’s particular distribution strategy.
Cyber criminals use the EternalBlue exploit that has been leaked from US National Security Agency (NSA) a month ago. This exploit allows targeting Windows CVE-2017-0145 vulnerability that affects Server Message Block (SBM) protocol. While Windows 10 users should not worry about this security flaw, others are in great danger. Malware aims at old, unpatched and unsupported Windows operating systems. Once it finds and affects the device, it continues spreading through the network and hijacking other vulnerable systems. Fortunately, Microsoft has already released a security bulletin MS17-010 and encourages users to download it immediately. The company took care of Windows XP, Vista, Windows 2003 and Windows 2008 users too, and provided them necessary security update for free. Such generosity from Microsoft should be especially appreciated by various companies, governmental institutions and other organizations that do not invest in latest technologies and cyber security in general. Losing files to WananCry is a disaster if victims do not have backups. This ransomware is undecryptable yet.
If you are lucky enough and haven’t encountered this cyber threat yet, you should not hesitate and make sure that all necessary updates and patches are installed on your device. Moreover, the major security vendors have also updated their software, and current variants of ransomware are identifiable. Thus, you should invest in security software or update your current one. Taking precautions nowadays are crucial! However, if you cannot access your files due to .wcry, .wncryt or .wncry file extension, and see a terrifying pop-up window asking to transfer from $300-$600, you have to solve this serious problem immediately. Probably, you have already heard numerous reasons why you should never pay the ransom to cyber criminals. However, we want to discourage you one more time. Furthermore, we would like to suggest you checking these instructions how to get rid of WannaCry safely.
