Red Cerber ransomware is the late Christmas present for all computer users all over the world by the developers of the notorious Cerber ransomware. In the offline world these kinds of gifts would be returned, but online the situation is quite complicated. The infamous file-encrypting virus has been updated for the first time in 2017. The cyber criminals had worked on developing new distribution methods and some other behavioral features after the attack.
Malware still mainly spreads via malicious email attachments; however, now it is distributed via Nemucod downloader and RIG-V exploit kit. Using Nemucod made Red Cerber virus harder to detect and helps to infect even more computer users. It hides malicious javascript file in various safe-looking documents that are packed in .zip or .rar archive. Cyber criminals launched hundreds of different campaigns to spread malware actively and found new ways to trick people into opening a fake invoice or other important documents. Once they do that, ransomware gets inside and starts its dirty job.
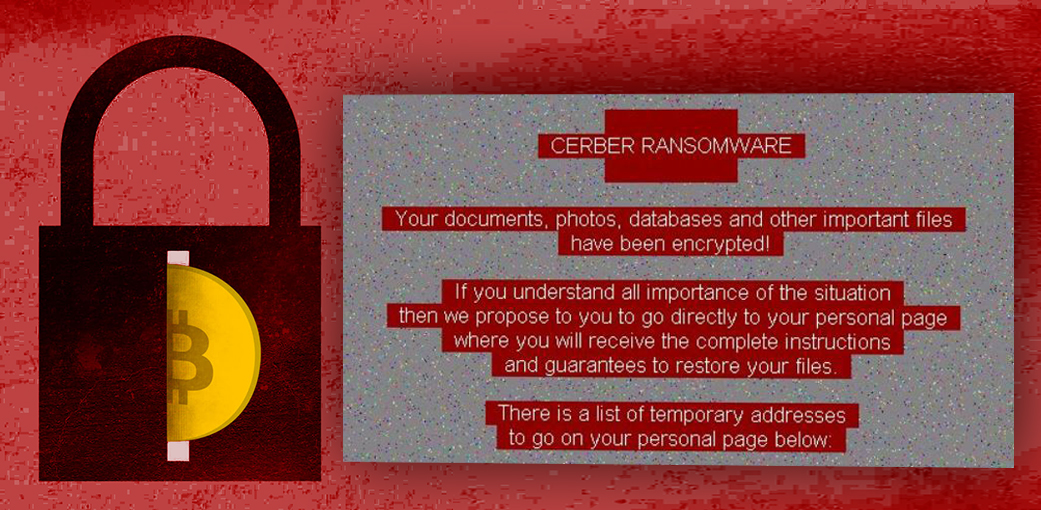
After infiltration Red Cerber ransomware virus scans for almost 500 targeted file types and encrypts them using strong encryption algorithm. To all encrypted files it appends a randomly generated four-character file extension and makes them useless. Generally, it behaves just like its counterparts: once data encryption is over, it leaves a ransom note where it demands to pay a particular amount of Bitcoins. Paying the ransom is never an option to get back access to the encrypted files; however, some users feel opposite and risk their money. If you are unlucky enough to encounter this ransomware, you should be aware that transferring the ransom might not be necessary. The newest version of Cerber does not delete Shadow Volume Copies. Therefore, if you have enabled System Restore function before ransomware attack, you should be able to restore at least the most important files.
It’s hard to tell why developers decided to make the latter change; however, they must have a valid reason. Even though now Cerber doesn’t look as dangerous and damaging as its predecessors, you should still treat it right. After the attack, do not focus on data recovery; remove Red Cerber from the device first. However, if you haven’t met this cyber parasite yet, stay safe online and backup your files!
