Diablo6 ransomware continues what Locky has started in 2016
The star of 2016 was updated one more time. On August 9th, 2017 security researcher discovered a new variant of Locky virus spreading via malicious spam emails. Malware appends .diablo6 file extension. Thus, it was named after it – Diablo6 ransomware virus.
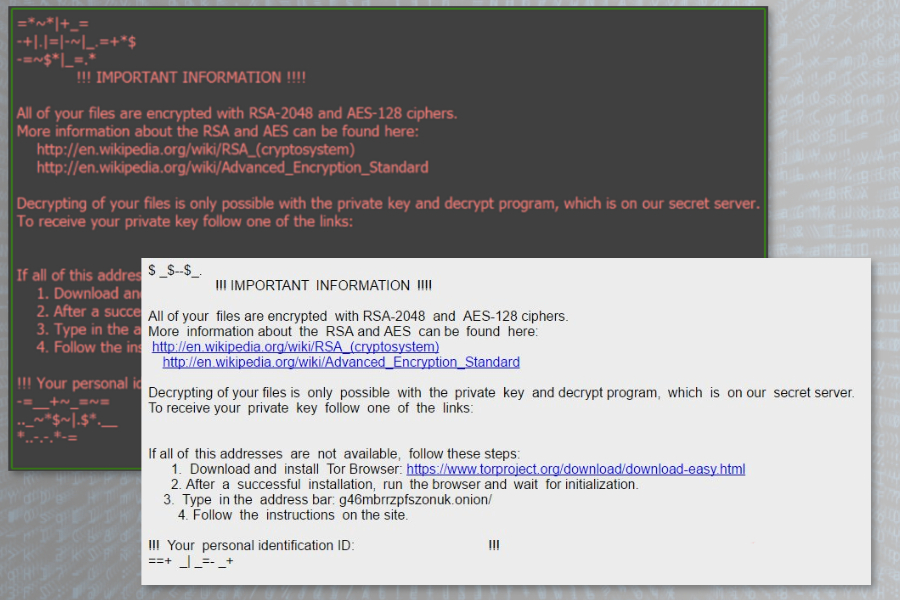
According to the latest analysis data, Diablo6 barely differs from the original malware. It uses a combination of RSA-2048 and AES-128 encryption algorithms and promoted Locky decryptor as the only tool that can help victims after the ransomware attack.
Unfortunately, files encrypted by Locky and all over its variants are still undecryptable. Therefore, data recovery is nearly impossible. However, backups can save valuable data and money. So, it’s time to copy new files and documents to external or cloud storage and learn how this recent cyber threat spreads.
Criminals spread Diablo6 via malicious spam emails
Traditions do not change. Developers of Locky are loyal to malspam as the main distribution strategy. This time criminals send ZIP archive with an email which subject line follows this scheme:
E [data] (random characters).docx
The malicious ZIP file has the same name too. The archive includes malicious VBS script that downloads and executes ransomware to the %Temp% folder. Once it’s done, malware launches the primary task – data encryption.
As we have mentioned before, ransomware uses RSA and AES cryptography and appends .diablo6 file extension. However, it also renames targeted data with the line of 32 characters, including unique victim’s ID provided in the ransom note. Thus, after the attack data is renamed following this path:
[first 8 characters of victim’s ID]-[next 4 characters of victim’s ID]-[next 4 characters of victim’s ID]-[4 random characters]-[12 random characters].diablo6
Diablo6 ransomware aims at the majority of files that are stored on the majority of users’ computers. The file-encrypting virus targets audio, video, text, archives, databases, documents and other data. Therefore, the attack is definitely painful for those who do not have backups.
After the attack Diablo6 ransomware installs two new files:
- diablo6.bmp
- diablo6-[random characters].htm
The .bmp file is a picture that replaces desktop’s background. The second file is a ransom note that provides links to same old Locky Decryptor website and demands to pay 0,49 Bitcoins.
Ransomware precautions and what to do after the attack
In order to avoid Diablo6 and other variants of Locky, you should be extremely careful with emails. You should never trust unknown senders that urge to open attachments or click on links.
Of course, social engineering helps crooks to become whoever they want. Thus, if you receive an unexpected letter from reputable company or organization, double-check the information about the issue in other sources.
However, authors of Locky proved that they could bypass Facebook’s security and reach social network users as well. Thus, you should be careful with all the links you see or receive online because malware can send the message with the help of one of your contacts.
Unfortunately, bad things happen to smart people too. In case of the attack, do not pay the ransom. Instead of that, remove Diablo6 from the device with security software. Talking about encrypted files, you can try additional tools, such as Data Recovery Pro, that might help to restore at least some of the files.
However, you can always backups encrypted files and follow the latest security news. Hopefully, security researchers will create safe and free software soon.
