Petya ransomware developers have once again caught the cyber community by surprise after a new and improved version of the virus started spreading havoc across the computers.
The virus was first spotted in Ukraine, where it paralyzed businesses and official institutions, locking computers and demanding 300 dollar payment for their decryption. Currently, Petya already holds hostage more than 2000 computers across the world. Attack reports flow from law firms, banks, healthcare institutions and organizations in Poland, UK, France, Italy, US and dozens of other countries. It seems that at least for now, there is virtually no way of immobilizing the threat.
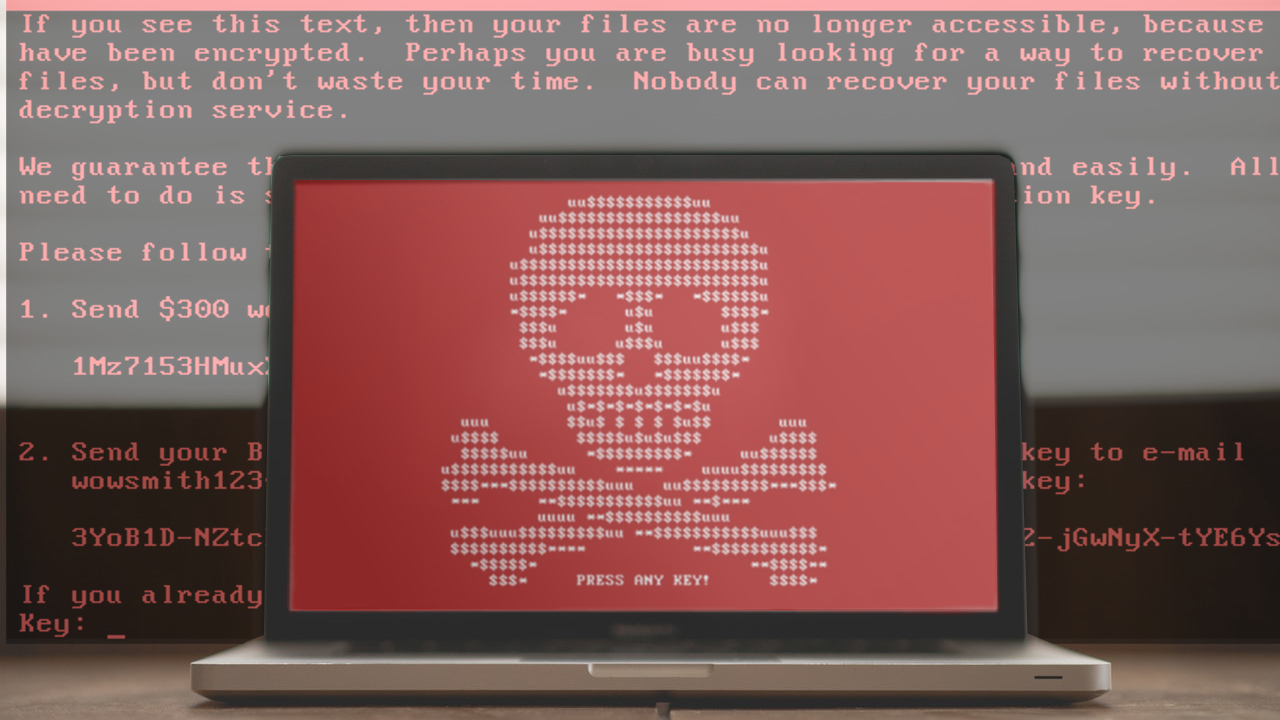
Talking about the ransomware itself, the parasite seems to have undergone quite significant changes. It looks different and applies new hijack techniques, unlike its previous versions. Because of that, some malware experts have even started inventing new names for this threat, referring to it as Petya.a, NotPetya, GoldenEye or Petrwrap.The virus now drops several types of files on the infected computers:
- its executable file ( petwrap.exe),
- ransom notes (Petya.a Virus.htm and Petya.a Virus.txt)
- and an image file (Petya.a Virus.bmp) that the virus uses to replace the regular desktop image.
The ransom notes can be found on all infected folders for easy access. These documents contain instructions explaining the process of data recovery.
We should warn you that even if you have become a victim of ransomware attack, you should collaborate with the criminals. You can’t be sure whether the criminals are going unlock your PC or simply vanish with your money and your hope for recovering your files. It is always a better option to remove the ransomware and wait for alternative data recovery keys to be invented.
When it comes to the malware distribution, the virus may use spam campaigns and even the simplest adware such as WinSnare, as long as it redirects the victims to the some infectious website where the virus payload can be downloaded to the computer.
It has already been confirmed that Petya employs the Eternal Blue tool infamously leaked from NSA’s secret databases and exploits zero day software vulnerabilities to get inside systems. This course of action is nearly identical to what we have witnessed during WannaCry that took place in May. We probably would not be wrong by saying that WannaCry’s success could have been the cause of the sudden Petya’s upsurge.
Petya virus is spreading rapidly and, at the moment, there is no “kill switch” to stop it. Home users, businesses, and institutions are advised to secure their computers networks, upgrade expired and no longer supported Windows versions to the latest ones and backup their data.
